最近小小的学习了一下内存取证,装环境搞了整整一天,非常麻烦,在阅读相关资料时偶然看到了一篇WriteUp,是关于OtterCTF2018 的十三道内存取证题目,用的全部是同一个镜像,考察的知识点非常全面,可以用来熟悉一下volatility的使用,关键是比赛平台居然还开着,正好当作内存取证的一次入门学习
What the password?
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 ┌──(root㉿kali2022)-[~] └─# vol.py -f /root/桌面/OtterCTF.vmem imageinfo Volatility Foundation Volatility Framework 2.6.1 INFO : volatility.debug : Determining profile based on KDBG search... Suggested Profile(s) : Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_24000, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_24000, Win7SP1x64_23418 AS Layer1 : WindowsAMD64PagedMemory (Kernel AS) AS Layer2 : FileAddressSpace (/root/桌面/OtterCTF.vmem) PAE type : No PAE DTB : 0x187000L KDBG : 0xf80002c430a0L Number of Processors : 2 Image Type (Service Pack) : 1 KPCR for CPU 0 : 0xfffff80002c44d00L KPCR for CPU 1 : 0xfffff880009ef000L KUSER_SHARED_DATA : 0xfffff78000000000L Image date and time : 2018-08-04 19:34:22 UTC+0000 Image local date and time : 2018-08-04 22:34:22 +0300
题目附件是一个raw文件,先用imageinfo查看一下镜像的信息,支持的系统有很多,我们可以试一试,指定profile为第一个Win7SP1x64,然后看看能否成功调用volshell
1 2 3 4 5 6 7 8 9 ┌──(root㉿kali2022)-[~] └─# vol.py -f /root/桌面/OtterCTF.vmem --profile=Win7SP1x64 volshell Volatility Foundation Volatility Framework 2.6.1 Current context: System @ 0xfffffa8018d44740, pid=4, ppid=0 DTB=0x187000 Welcome to volshell! Current memory image is: file:///root/%E6%A1%8C%E9%9D%A2/OtterCTF.vmem To get help, type 'hh()' > >> hh()
得到正确的镜像系统后,便可以在后面加上--profile=Win7SP1x64来使用后续的命令,第一题需要我们获取这个镜像的用户密码,可以使用hashdump,但得到密码都是哈希加密之后的,使用lsadump或者mimikatz可以得到明文
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 ┌──(root㉿kali2022)-[~] └─# vol.py -f /root/桌面/OtterCTF.vmem --profile=Win7SP1x64 hashdump Volatility Foundation Volatility Framework 2.6.1 Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Rick:1000:aad3b435b51404eeaad3b435b51404ee:518172d012f97d3a8fcc089615283940::: ┌──(root㉿kali2022)-[~] └─# vol.py -f /root/桌面/OtterCTF.vmem --profile=Win7SP1x64 lsadump Volatility Foundation Volatility Framework 2.6.1 DefaultPassword 0x00000000 28 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 (............... 0x00000010 4d 00 6f 00 72 00 74 00 79 00 49 00 73 00 52 00 M.o.r.t.y.I.s.R. 0x00000020 65 00 61 00 6c 00 6c 00 79 00 41 00 6e 00 4f 00 e.a.l.l.y.A.n.O. 0x00000030 74 00 74 00 65 00 72 00 00 00 00 00 00 00 00 00 t.t.e.r......... DPAPI_SYSTEM 0x00000000 2c 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ,............... 0x00000010 01 00 00 00 36 9b ba a9 55 e1 92 82 09 e0 63 4c ....6...U.....cL 0x00000020 20 74 63 14 9e d8 a0 4b 45 87 5a e4 bc f2 77 a5 .tc....KE.Z...w. 0x00000030 25 3f 47 12 0b e5 4d a5 c8 35 cf dc 00 00 00 00 %?G...M..5...... ┌──(root㉿kali2022)-[~] └─# vol.py -f /root/桌面/OtterCTF.vmem --profile=Win7SP1x64 mimikatz Volatility Foundation Volatility Framework 2.6.1 Module User Domain Password -------- ---------------- ---------------- ---------------------------------------- wdigest Rick WIN-LO6FAF3DTFE MortyIsReallyAnOtter wdigest WIN-LO6FAF3DTFE$ WORKGROUP
CTF{MortyIsReallyAnOtter}
General Info
第二题要获取主机名和ip地址
ip地址
能获取的ip地址的最快办法就是netscan,查看网络连接
1 2 3 4 5 6 7 8 9 10 ┌──(root㉿kali2022)-[~] └─# vol.py -f /root/桌面/OtterCTF.vmem --profile=Win7SP1x64 netscan Volatility Foundation Volatility Framework 2.6.1 Offset(P) Proto Local Address Foreign Address State Pid Owner Created 0x7d60f010 UDPv4 0.0.0.0:1900 *:* 2836 BitTorrent.exe 2018-08-04 19:27:17 UTC+0000 0x7d62b3f0 UDPv4 192.168.202.131:6771 *:* 2836 BitTorrent.exe 2018-08-04 19:27:22 UTC+0000 0x7d62f4c0 UDPv4 127.0.0.1:62307 *:* 2836 BitTorrent.exe 2018-08-04 19:27:17 UTC+0000 0x7d62f920 UDPv4 192.168.202.131:62306 *:* 2836 BitTorrent.exe 2018-08-04 19:27:17 UTC+0000 ...... ......
netscan的结果很多,这里只放了一部分,期中多次出现的192.168.202.131就是ip地址
主机名
主机名的获取方法有两种,第一种是直接在hashdump的显示中可以看到主机名,第二种就是查注册表,这里使用hivelist查注册表
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 ┌──(root㉿kali2022)-[~] └─# vol.py -f /root/桌面/OtterCTF.vmem --profile=Win7SP1x64 hivelist Volatility Foundation Volatility Framework 2.6.1 Virtual Physical Name ------------------ ------------------ ---- 0xfffff8a00377d2d0 0x00000000624162d0 \??\C:\System Volume Information\Syscache.hve 0xfffff8a00000f010 0x000000002d4c1010 [no name] 0xfffff8a000024010 0x000000002d50c010 \REGISTRY\MACHINE\SYSTEM 0xfffff8a000053320 0x000000002d5bb320 \REGISTRY\MACHINE\HARDWARE 0xfffff8a000109410 0x0000000029cb4410 \SystemRoot\System32\Config\SECURITY 0xfffff8a00033d410 0x000000002a958410 \Device\HarddiskVolume1\Boot\BCD 0xfffff8a0005d5010 0x000000002a983010 \SystemRoot\System32\Config\SOFTWARE 0xfffff8a001495010 0x0000000024912010 \SystemRoot\System32\Config\DEFAULT 0xfffff8a0016d4010 0x00000000214e1010 \SystemRoot\System32\Config\SAM 0xfffff8a00175b010 0x00000000211eb010 \??\C:\Windows\ServiceProfiles\NetworkService\NTUSER.DAT 0xfffff8a00176e410 0x00000000206db410 \??\C:\Windows\ServiceProfiles\LocalService\NTUSER.DAT 0xfffff8a002090010 0x000000000b92b010 \??\C:\Users\Rick\ntuser.dat 0xfffff8a0020ad410 0x000000000db41410 \??\C:\Users\Rick\AppData\Local\Microsoft\Windows\UsrClass.dat
主机名信息在system的那一条记录中,再用-o + 地址 printkey 来查看指定的记录
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 ┌──(root㉿kali2022)-[~] └─# vol.py -f /root/桌面/OtterCTF.vmem --profile=Win7SP1x64 -o 0xfffff8a000024010 printkey Volatility Foundation Volatility Framework 2.6.1 Legend: (S) = Stable (V) = Volatile ---------------------------- Registry: \REGISTRY\MACHINE\SYSTEM Key name: CMI-CreateHive{2A7FB991-7BBE-4F9D-B91E-7CB51D4737F5} (S) Last updated: 2018-08-04 19:25:54 UTC+0000 Subkeys: (S) ControlSet001 (S) ControlSet002 (S) MountedDevices (S) RNG (S) Select (S) Setup (S) Software (S) WPA (V) CurrentControlSet Values:
跟进ControlSet001,一路到最后可以看到主机名的value
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 ┌──(root㉿kali2022)-[~] └─# vol.py -f /root/桌面/OtterCTF.vmem --profile=Win7SP1x64 -o 0xfffff8a000024010 printkey -K "ControlSet001\Control\ComputerName\ComputerName" Volatility Foundation Volatility Framework 2.6.1 Legend: (S) = Stable (V) = Volatile ---------------------------- Registry: \REGISTRY\MACHINE\SYSTEM Key name: ComputerName (S) Last updated: 2018-06-02 19:23:00 UTC+0000 Subkeys: Values: REG_SZ : (S) mnmsrvc REG_SZ ComputerName : (S) WIN-LO6FAF3DTFE
CTF{192.168.202.131}
CTF{WIN-LO6FAF3DTFE}
Play Time
要找到他玩的游戏,可以用pslist来看看进程,看ip地址可以用netscan
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 ┌──(root㉿kali2022)-[~] └─# vol.py -f /root/桌面/OtterCTF.vmem --profile=Win7SP1x64 pslist Volatility Foundation Volatility Framework 2.6.1 Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit ------------------ -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------ 0xfffffa8018d44740 System 4 0 95 411 ------ 0 2018-08-04 19:26:03 UTC+0000 0xfffffa801947e4d0 smss.exe 260 4 2 30 ------ 0 2018-08-04 19:26:03 UTC+0000 0xfffffa801a0c8380 csrss.exe 348 336 9 563 0 0 2018-08-04 19:26:10 UTC+0000 ...... ...... 0xfffffa801b4a7b30 bittorrentie.e 2308 2836 15 337 1 1 2018-08-04 19:27:19 UTC+0000 0xfffffa801b4c9b30 bittorrentie.e 2624 2836 13 316 1 1 2018-08-04 19:27:21 UTC+0000 0xfffffa801b5cb740 LunarMS.exe 708 2728 18 346 1 1 2018-08-04 19:27:39 UTC+0000 0xfffffa801988c2d0 PresentationFo 724 492 6 148 0 0 2018-08-04 19:27:52 UTC+0000 ...... ......
其中有个进程LunarMS.exe,可以谷歌搜索一下,发现是个游戏,顺势用netscan查出ip地址
1 2 3 4 5 6 ┌──(root㉿kali2022)-[~] └─# vol.py -f /root/桌面/OtterCTF.vmem --profile=Win7SP1x64 netscan|grep LunarMS Volatility Foundation Volatility Framework 2.6.1 0x7d6124d0 TCPv4 192.168.202.131:49530 77.102.199.102:7575 CLOSED 708 LunarMS.exe 0x7e413a40 TCPv4 -:0 -:0 CLOSED 708 LunarMS.exe 0x7e521b50 TCPv4 -:0 -:0 CLOSED 708 LunarMS.exe
CTF{LunarMS}
CTF{77.102.199.102}
Name Game
要找到Lunar-3这个服上的用户名,我们最好把进程给dump下来进行逆向分析,这里也可以在镜像中通过寻找字符串的方式找到和Lunar-3相关记录
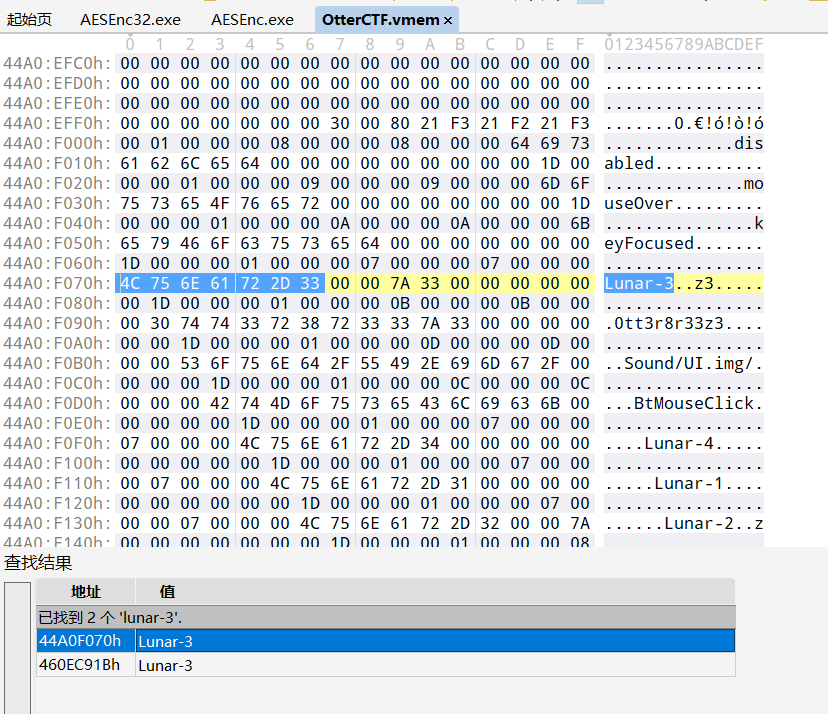
这里可以使用工具010editor
可以看到Lunar-3的后面有一个奇怪的字符串0tt3r8r33z3,这个就是用户名
或者也可以在命令行中直接查找
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 ┌──(root㉿kali2022)-[~] └─# strings /root/桌面/OtterCTF.vmem|grep Lunar-3 -C 5 .>SWqn Y!F[Wq disabled mouseOver keyFocused Lunar-3 0tt3r8r33z3 Sound/UI.img/ BtMouseClick Lunar-4 Lunar-1 -- c+Y\ \b+Y c+Yt tb+Y4c+Y b+YLc+Y Lunar-3 Lunar-4 L(dNVxdNV L|eNV {qf8 q r"r r
这里使用strings命令加上grep搜索,-C 5表示查找前后5条记录,同样可以找到可疑字符串
CTF{0tt3r8r33z3}
Name Game 2
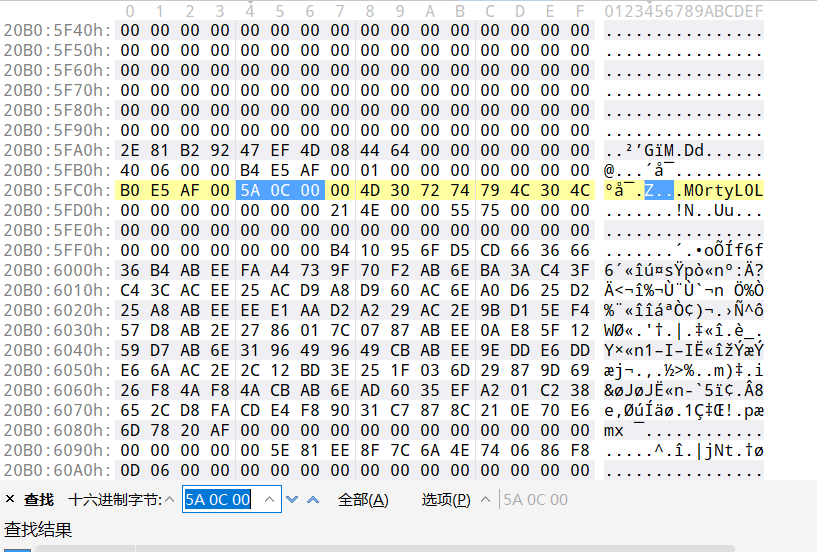
这里先用memdump把前面那个LunarMS.exe游戏进程打印出来,进程号PID可以看前面的pslist
1 2 3 4 5 6 ┌──(root㉿kali2022)-[~] └─# vol.py -f /root/桌面/OtterCTF.vmem --profile=Win7SP1x64 memdump -p 708 -D ./ Volatility Foundation Volatility Framework 2.6.1 ************************************************************************ Writing LunarMS.exe [ 708] to 708.dmp
这个题给了一个16进制的签名,我们用010来搜索其中的片段5A 0C 00,结果非常多,得慢慢找,可以看到这个M0rtyL0L就是角色名
用hexdump命令也可以查找,结果就不放了,太长了
1 hexdump -C 708.dmp |grep "5a 0c 00" -A 3 -B 3
CTF{M0rtyL0L}
Silly Rick
题目需要获得邮箱密码,又提示说经常复制粘贴,那我们可以用clipboard查看剪贴板
1 2 3 4 5 6 7 8 9 10 11 ┌──(root㉿kali2022)-[~] └─# vol.py -f /root/桌面/OtterCTF.vmem --profile=Win7SP1x64 clipboard Volatility Foundation Volatility Framework 2.6.1 Session WindowStation Format Handle Object Data ---------- ------------- ------------------ ------------------ ------------------ -------------------------------------------------- 1 WinSta0 CF_UNICODETEXT 0x602e3 0xfffff900c1ad93f0 M@il_Pr0vid0rs 1 WinSta0 CF_TEXT 0x10 ------------------ 1 WinSta0 0x150133L 0x200000000000 ------------------ 1 WinSta0 CF_TEXT 0x1 ------------------ 1 ------------- ------------------ 0x150133 0xfffff900c1c1adc0
CTF{M@il_Pr0vid0rs}
Hide And Seek
这个题目要找到恶意进程名字,我们可以用pstree查看进程树
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 ┌──(root㉿kali2022)-[~] └─# vol.py -f /root/桌面/OtterCTF.vmem --profile=Win7SP1x64 pstree Volatility Foundation Volatility Framework 2.6.1 Name Pid PPid Thds Hnds Time -------------------------------------------------- ------ ------ ------ ------ ---- 0xfffffa801b27e060:explorer.exe 2728 2696 33 854 2018-08-04 19:27:04 UTC+0000 . 0xfffffa801b486b30:Rick And Morty 3820 2728 4 185 2018-08-04 19:32:55 UTC+0000 .. 0xfffffa801a4c5b30:vmware-tray.ex 3720 3820 8 147 2018-08-04 19:33:02 UTC+0000 . 0xfffffa801b2f02e0:WebCompanion.e 2844 2728 0 ------ 2018-08-04 19:27:07 UTC+0000 . 0xfffffa801a4e3870:chrome.exe 4076 2728 44 1160 2018-08-04 19:29:30 UTC+0000 .. 0xfffffa801a4eab30:chrome.exe 4084 4076 8 86 2018-08-04 19:29:30 UTC+0000 .. 0xfffffa801a5ef1f0:chrome.exe 1796 4076 15 170 2018-08-04 19:33:41 UTC+0000 .. 0xfffffa801aa00a90:chrome.exe 3924 4076 16 228 2018-08-04 19:29:51 UTC+0000 .. 0xfffffa801a635240:chrome.exe 3648 4076 16 207 2018-08-04 19:33:38 UTC+0000 .. 0xfffffa801a502b30:chrome.exe 576 4076 2 58 2018-08-04 19:29:31 UTC+0000 .. 0xfffffa801a4f7b30:chrome.exe 1808 4076 13 229 2018-08-04 19:29:32 UTC+0000 .. 0xfffffa801a7f98f0:chrome.exe 2748 4076 15 181 2018-08-04 19:31:15 UTC+0000 . 0xfffffa801b5cb740:LunarMS.exe 708 2728 18 346 2018-08-04 19:27:39 UTC+0000 . 0xfffffa801b1cdb30:vmtoolsd.exe 2804 2728 6 190 2018-08-04 19:27:06 UTC+0000 . 0xfffffa801b290b30:BitTorrent.exe 2836 2728 24 471 2018-08-04 19:27:07 UTC+0000 .. 0xfffffa801b4c9b30:bittorrentie.e 2624 2836 13 316 2018-08-04 19:27:21 UTC+0000 .. 0xfffffa801b4a7b30:bittorrentie.e 2308 2836 15 337 2018-08-04 19:27:19 UTC+0000 0xfffffa8018d44740:System 4 0 95 411 2018-08-04 19:26:03 UTC+0000 . 0xfffffa801947e4d0:smss.exe 260 4 2 30 2018-08-04 19:26:03 UTC+0000 0xfffffa801a2ed060:wininit.exe 396 336 3 78 2018-08-04 19:26:11 UTC+0000 . 0xfffffa801ab377c0:services.exe 492 396 11 242 2018-08-04 19:26:12 UTC+0000 .. 0xfffffa801afe7800:svchost.exe 1948 492 6 96 2018-08-04 19:26:42 UTC+0000 .. 0xfffffa801ae92920:vmtoolsd.exe 1428 492 9 313 2018-08-04 19:26:27 UTC+0000 ... 0xfffffa801a572b30:cmd.exe 3916 1428 0 ------ 2018-08-04 19:34:22 UTC+0000 .. 0xfffffa801ae0f630:VGAuthService. 1356 492 3 85 2018-08-04 19:26:25 UTC+0000 .. 0xfffffa801abbdb30:vmacthlp.exe 668 492 3 56 2018-08-04 19:26:16 UTC+0000 .. 0xfffffa801aad1060:Lavasoft.WCAss 3496 492 14 473 2018-08-04 19:33:49 UTC+0000 .. 0xfffffa801a6af9f0:svchost.exe 164 492 12 147 2018-08-04 19:28:42 UTC+0000 .. 0xfffffa801ac2e9e0:svchost.exe 808 492 22 508 2018-08-04 19:26:18 UTC+0000 ... 0xfffffa801ac753a0:audiodg.exe 960 808 7 151 2018-08-04 19:26:19 UTC+0000 .. 0xfffffa801ae7f630:dllhost.exe 1324 492 15 207 2018-08-04 19:26:42 UTC+0000 .. 0xfffffa801a6c2700:mscorsvw.exe 3124 492 7 77 2018-08-04 19:28:43 UTC+0000 .. 0xfffffa801b232060:sppsvc.exe 2500 492 4 149 2018-08-04 19:26:58 UTC+0000 .. 0xfffffa801abebb30:svchost.exe 712 492 8 301 2018-08-04 19:26:17 UTC+0000 .. 0xfffffa801ad718a0:svchost.exe 1164 492 18 312 2018-08-04 19:26:23 UTC+0000 .. 0xfffffa801ac31b30:svchost.exe 844 492 17 396 2018-08-04 19:26:18 UTC+0000 ... 0xfffffa801b1fab30:dwm.exe 2704 844 4 97 2018-08-04 19:27:04 UTC+0000 .. 0xfffffa801988c2d0:PresentationFo 724 492 6 148 2018-08-04 19:27:52 UTC+0000 .. 0xfffffa801b603610:mscorsvw.exe 412 492 7 86 2018-08-04 19:28:42 UTC+0000 .. 0xfffffa8018e3c890:svchost.exe 604 492 11 376 2018-08-04 19:26:16 UTC+0000 ... 0xfffffa8019124b30:WmiPrvSE.exe 1800 604 9 222 2018-08-04 19:26:39 UTC+0000 ... 0xfffffa801b112060:WmiPrvSE.exe 2136 604 12 324 2018-08-04 19:26:51 UTC+0000 .. 0xfffffa801ad5ab30:spoolsv.exe 1120 492 14 346 2018-08-04 19:26:22 UTC+0000 .. 0xfffffa801ac4db30:svchost.exe 868 492 45 1114 2018-08-04 19:26:18 UTC+0000 .. 0xfffffa801a6e4b30:svchost.exe 3196 492 14 352 2018-08-04 19:28:44 UTC+0000 .. 0xfffffa801acd37e0:svchost.exe 620 492 19 415 2018-08-04 19:26:21 UTC+0000 .. 0xfffffa801b1e9b30:taskhost.exe 2344 492 8 193 2018-08-04 19:26:57 UTC+0000 .. 0xfffffa801ac97060:svchost.exe 1012 492 12 554 2018-08-04 19:26:20 UTC+0000 .. 0xfffffa801b3aab30:SearchIndexer. 3064 492 11 610 2018-08-04 19:27:14 UTC+0000 .. 0xfffffa801aff3b30:msdtc.exe 1436 492 14 155 2018-08-04 19:26:43 UTC+0000 . 0xfffffa801ab3f060:lsass.exe 500 396 7 610 2018-08-04 19:26:12 UTC+0000 . 0xfffffa801ab461a0:lsm.exe 508 396 10 148 2018-08-04 19:26:12 UTC+0000 0xfffffa801a0c8380:csrss.exe 348 336 9 563 2018-08-04 19:26:10 UTC+0000 . 0xfffffa801a6643d0:conhost.exe 2420 348 0 30 2018-08-04 19:34:22 UTC+0000 0xfffffa80198d3b30:csrss.exe 388 380 11 460 2018-08-04 19:26:11 UTC+0000 0xfffffa801aaf4060:winlogon.exe 432 380 3 113 2018-08-04 19:26:11 UTC+0000 0xfffffa801b18f060:WebCompanionIn 3880 1484 15 522 2018-08-04 19:33:07 UTC+0000 . 0xfffffa801aa72b30:sc.exe 3504 3880 0 ------ 2018-08-04 19:33:48 UTC+0000 . 0xfffffa801aeb6890:sc.exe 452 3880 0 ------ 2018-08-04 19:33:48 UTC+0000 . 0xfffffa801a6268b0:WebCompanion.e 3856 3880 15 386 2018-08-04 19:34:05 UTC+0000 . 0xfffffa801b08f060:sc.exe 3208 3880 0 ------ 2018-08-04 19:33:47 UTC+0000 . 0xfffffa801ac01060:sc.exe 2028 3880 0 ------ 2018-08-04 19:33:49 UTC+0000 0xfffffa801b1fd960:notepad.exe 3304 3132 2 79 2018-08-04 19:34:10 UTC+0000
其中有个很奇怪的vmware-tray.exe居然是Rick And Morty的子进程,非常奇怪,
可以用dlllist查看一下进程相关的dll文件列表
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 ┌──(root㉿kali2022)-[~] └─# vol.py -f /root/桌面/OtterCTF.vmem --profile=Win7SP1x64 dlllist -p 3720 Volatility Foundation Volatility Framework 2.6.1 ************************************************************************ vmware-tray.ex pid: 3720 Command line : "C:\Users\Rick\AppData\Local\Temp\RarSFX0\vmware-tray.exe" Base Size LoadCount LoadTime Path ------------------ ------------------ ------------------ ------------------------------ ---- 0x0000000000ec0000 0x6e000 0xffff 1970-01-01 00:00:00 UTC+0000 C:\Users\Rick\AppData\Local\Temp\RarSFX0\vmware-tray.exe 0x00000000776f0000 0x1a9000 0xffff 1970-01-01 00:00:00 UTC+0000 C:\Windows\SYSTEM32\ntdll.dll 0x0000000075210000 0x3f000 0x3 2018-08-04 19:33:03 UTC+0000 C:\Windows\SYSTEM32\wow64.dll 0x00000000751b0000 0x5c000 0x1 2018-08-04 19:33:03 UTC+0000 C:\Windows\SYSTEM32\wow64win.dll 0x00000000751a0000 0x8000 0x1 2018-08-04 19:33:03 UTC+0000 C:\Windows\SYSTEM32\wow64cpu.dll 0x0000000000ec0000 0x6e000 0xffff 1970-01-01 00:00:00 UTC+0000 C:\Users\Rick\AppData\Local\Temp\RarSFX0\vmware-tray.exe 0x00000000778d0000 0x180000 0xffff 1970-01-01 00:00:00 UTC+0000 C:\Windows\SysWOW64\ntdll.dll ...... ......
这个进程的执行目录是temp,一看就不是正经程序
CTF{vmware-tray.exe}
Path To Glory
这个题目有点意义不明,不明确flag内容到底应该是什么
由于上一题了解到,恶意进程的父进程是Rick And Morty,那么先用filescan找一找这个文件
1 2 3 4 5 6 7 8 9 10 ┌──(root㉿kali2022)-[~] └─# vol.py -f /root/桌面/OtterCTF.vmem --profile=Win7SP1x64 filescan|grep 'Rick And Morty' Volatility Foundation Volatility Framework 2.6.1 0x000000007d63dbc0 10 0 R--r-d \Device\HarddiskVolume1\Torrents\Rick And Morty season 1 download.exe 0x000000007d8813c0 2 0 RW-rwd \Device\HarddiskVolume1\Users\Rick\Downloads\Rick And Morty season 1 download.exe.torrent 0x000000007da56240 2 0 RW-rwd \Device\HarddiskVolume1\Torrents\Rick And Morty season 1 download.exe 0x000000007dae9350 2 0 RWD--- \Device\HarddiskVolume1\Users\Rick\AppData\Roaming\BitTorrent\Rick And Morty season 1 download.exe.1.torrent 0x000000007dcbf6f0 2 0 RW-rwd \Device\HarddiskVolume1\Users\Rick\AppData\Roaming\BitTorrent\Rick And Morty season 1 download.exe.1.torrent 0x000000007e710070 8 0 R--rwd \Device\HarddiskVolume1\Torrents\Rick And Morty season 1 download.exe
一共6个文件,其中有三个exe和三个种子文件,我们要分析来源就要关注种子文件,里面可能放着地址信息
先用dumpfiles转储文件,-Q指定内存地址,把三个种子都拿出来分析
1 2 3 4 5 ┌──(root㉿kali2022)-[~] └─# vol.py -f /root/桌面/OtterCTF.vmem --profile=Win7SP1x64 dumpfiles -Q 0x000000007d8813c0 -D ./ Volatility Foundation Volatility Framework 2.6.1 DataSectionObject 0x7d8813c0 None \Device\HarddiskVolume1\Users\Rick\Downloads\Rick And Morty season 1 download.exe.torrent
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 ┌──(root㉿kali2022)-[~] └─# strings file.None.0xfffffa801af10010.dat [ZoneTransfer] ZoneId=3 ┌──(root㉿kali2022)-[~] └─# strings file.None.0xfffffa801b42c9e0.dat d8:announce44:udp://tracker.openbittorrent.com:80/announce13:announce-listll44:udp://tracker.openbittorrent.com:80/announceel42:udp://tracker.opentrackr.org:1337/announceee10:created by17:BitTorrent/7.10.313:creation datei1533150595e8:encoding5:UTF-84:infod6:lengthi456670e4:name36:Rick And Morty season 1 download.exe12:piece lengthi16384e6:pieces560:\I !PC<^X B.k_Rk 0<;O87o !4^" 3hq, &iW1| K68:o w~Q~YT $ $o9p bwF:u e7:website19:M3an_T0rren7_4_R!cke ┌──(root㉿kali2022)-[~] └─# strings file.None.0xfffffa801b51ccf0.dat [ZoneTransfer] ZoneId=3
第二个种子文件中有个website字段M3an_T0rren7_4_R!cke非常可疑
当作答案提交一下,结果错了,最后上网发现末尾的e是没有的,我也不知道为啥
CTF{M3an_T0rren7_4_R!ck}
Path To Glory 2
这个题目更迷了,猜不透让我交啥,这里我看了一下网上办法
先把所有的chrome浏览器进程转储下来,
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 ┌──(root㉿kali2022)-[~] └─# vol.py -f /root/桌面/OtterCTF.vmem --profile=Win7SP1x64 memdump -n chrome.exe -D ./chrome Volatility Foundation Volatility Framework 2.6.1 ************************************************************************ Writing chrome.exe [ 4076] to 4076.dmp ************************************************************************ Writing chrome.exe [ 4084] to 4084.dmp ************************************************************************ Writing chrome.exe [ 576] to 576.dmp ************************************************************************ Writing chrome.exe [ 1808] to 1808.dmp ************************************************************************ Writing chrome.exe [ 3924] to 3924.dmp ************************************************************************ Writing chrome.exe [ 2748] to 2748.dmp ************************************************************************ Writing chrome.exe [ 3648] to 3648.dmp ************************************************************************ Writing chrome.exe [ 1796] to 1796.dmp
再看看有没有和Rick And Morty相关的信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 ┌──(root㉿kali2022)-[~] └─# strings ./chrome/* | grep 'Rick And Morty season 1 download.exe' -C 10 ...... ...... -- wCachePathe .CachePrefix CacheLimite CacheOptions CacheRepair GOOGLE~1.LNK MAPLES~1.URL BITTOR~1.LNK Flag.txt Flag.txt Rick And Morty season 1 download.exe.lnk Rick And Morty season 1 download.exe.lnk .WINDOWS OpenWithListp {1NP14R77-02R7-4R5Q-O744-2RO1NR5198O7}\ehaqyy32.rkr MRUList .WINDOWS .tor .txt .WIN .ziphx Foldv -- ...... ...... -- display:inline;width:56px;height:200px;m> Hum@n_I5_Th3_Weak3s7_Link_In_Th3_Ch@inYear //sec-s.uicdn.com/nav-cdn/home/preloader.gif simple-icon_toolbar-change-view-horizontal nnx-track-sec-click-communication-inboxic.com nx-track-sec-click-dashboard-hide_smileyable Nftd-box stem-north big fullsize js-focusable js-box-flex need-overlay js-componentone Jhttps://search.mail.com/web [q origin ]Year ntrack-and-trace__delivery-info--has-iconf Rick And Morty season 1 download.exe.torrent tbl_1533411035475_7.0.1.40728_2033115181 panel-mail-display-table-mail-default35" Cnpanel-mail-display-table-mail-horizontal.js trc_rbox text-links-a trc-content-sponsored identity_OjpwcmVsb2FkZXIuaHRtbC50d2ln Move the widget to its desired position.3c8= Set-Cookie, no-store, proxy-revalidateHxRKw= Set-Cookie, no-store, proxy-revalidate143/ tbl_1533411035475_7.0.9.40728_2033115181 "mail.com Update" <service@corp.mail.com>e ...... ......
找到的结果中Hum@n_I5_Th3_Weak3s7_Link_In_Th3_Ch@in即为flag,然后结果中意外的发现了flag.txt,后面会用到
CTF{Hum@n_I5_Th3_Weak3s7_Link_In_Th3_Ch@in}
Bit 4 Bit
题目告诉我们这个恶意进程是一个勒索软件,要我们找出攻击者的比特币账户地址,那我们肯定是要先把恶意软件dump下来
1 2 3 4 5 6 7 ┌──(root㉿kali2022)-[~] └─# vol.py -f /root/桌面/OtterCTF.vmem --profile=Win7SP1x64 procdump -p 3720 -D ./ Volatility Foundation Volatility Framework 2.6.1 Process(V) ImageBase Name Result ------------------ ------------------ -------------------- ------ 0xfffffa801a4c5b30 0x0000000000ec0000 vmware-tray.ex OK: executable.3720.exe
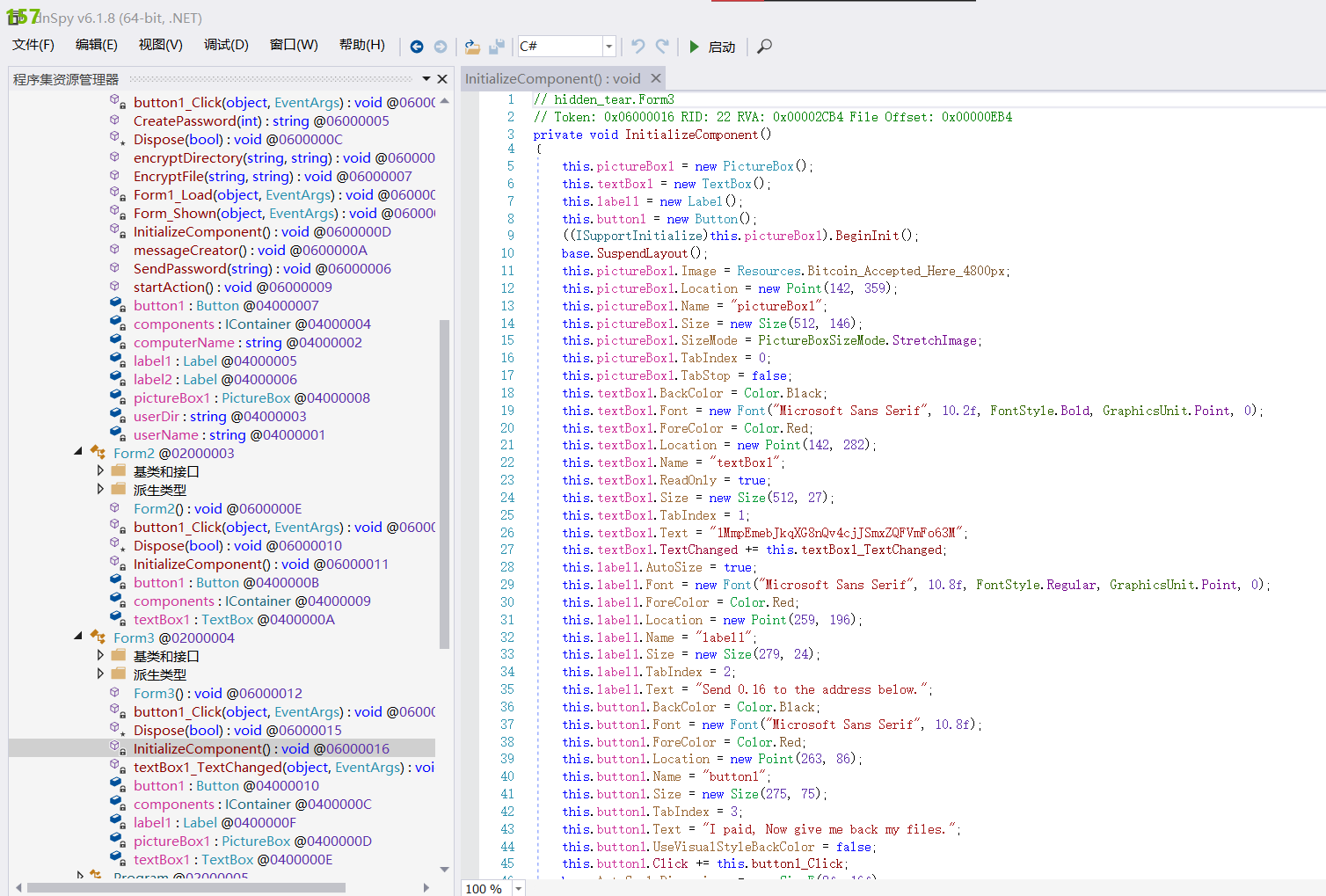
接下来就是用dnspy进行逆向分析(直接看伪代码)
在form3中可以看到这个软件的显示的信息,直接把address写出来了
CTF{1MmpEmebJkqXG8nQv4cjJSmxZQFVmFo63M}
Graphic’s For The Weak
要找到图片的隐藏信息,那就继续分析,在资源中查看图片,直接可以看到隐藏信息
CTF{S0_Just_M0v3_Socy}
Recovery
这一题就是找出加密文件所使用的密码
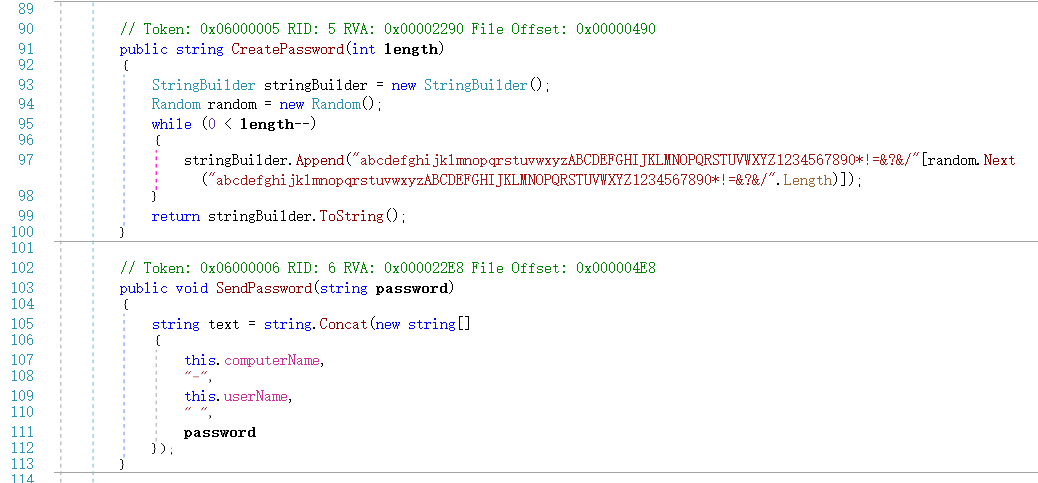
分析exe可以看到两个函数,第一个创建密码是随机的,然后有一个发送密码,是把computerName和userName还有password拼接以后进行发送
可以分析出compuerName就是WIN-LO6FAF3DTFE,用户名是Rick,所以这个函数发送的字符串应该是WIN-LO6FAF3DTFE-Rick password,我们直接去这个勒索软件的内存中寻找相关字符串即可
1 2 3 4 5 6 7 8 9 10 11 12 13 14 ┌──(root㉿kali2022)-[~] └─# strings -el ./3720.dmp | grep 'WIN-LO6FAF3DTFE-Rick' -C 5 \Desktop\ abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890*!=&?&/ aDOBofVYUNVnmp7 aDOBofVYUNVnmp7 C:\Users\Rick\Desktop\ WIN-LO6FAF3DTFE-Rick aDOBofVYUNVnmp7 .txt .doc .docx .xls .xlsx
-el参数的e指定了字符编码,l为小端编码,如果想用大端就是-eb
这里搜索到的aDOBofVYUNVnmp7就是password
CTF{aDOBofVYUNVnmp7}
Closure
最后一题要解密文件,容易想到前面提到的flag文件,这个flag文件应该是被加密过的,但我们已经知道密码了
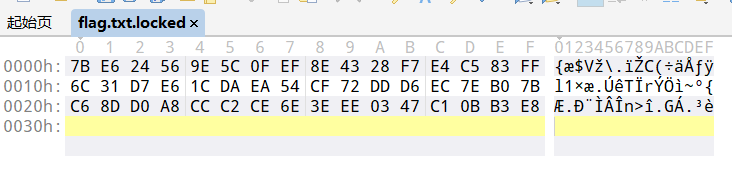
1 2 3 4 5 6 7 8 9 10 11 ┌──(root㉿kali2022)-[~] └─# vol.py -f /root/桌面/OtterCTF.vmem --profile=Win7SP1x64 filescan|grep -i 'flag' Volatility Foundation Volatility Framework 2.6.1 0x000000007d61b070 16 0 RW-rw- \Device\HarddiskVolume1\Users\Rick\AppData\Roaming\Microsoft\Windows\Recent\Flag.txt.WINDOWS.lnk 0x000000007e410890 16 0 R--r-- \Device\HarddiskVolume1\Users\Rick\Desktop\Flag.txt ┌──(root㉿kali2022)-[~] └─# vol.py -f /root/桌面/OtterCTF.vmem --profile=Win7SP1x64 dumpfiles -Q 0x000000007e410890 -D ./ Volatility Foundation Volatility Framework 2.6.1 DataSectionObject 0x7e410890 None \Device\HarddiskVolume1\Users\Rick\Desktop\Flag.txt
先找到flag文件,并且转储下来
解密过程
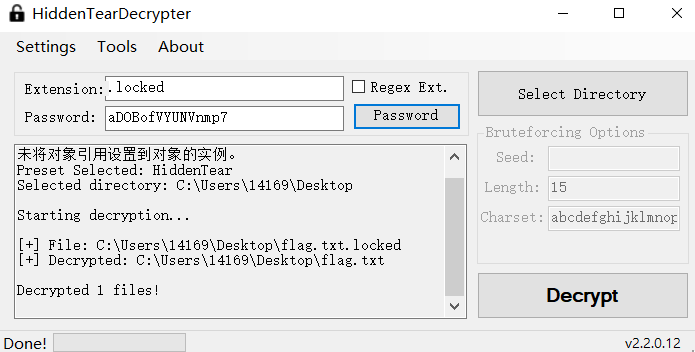
已知这个勒索软件为HiddenTear,直接在网上找到解密程序HiddenTearDecrypter
先将加密文件的末尾多余的0去掉,再把后缀加上locked
拿去解密,密钥已经知道了,直接输入
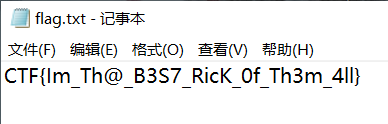
CTF{Im_Th@_B3S7_RicK_0f_Th3m_4ll}